Understanding Web Shell Backdoors: Risks, Prevention, and Detection
What are web shell backdoors?
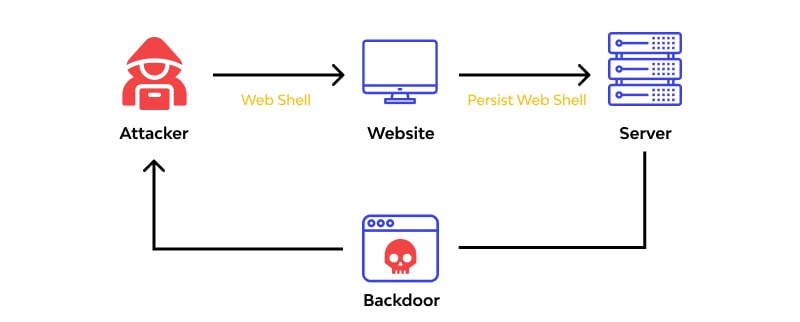
Web shell backdoors are malicious pieces of code (e.g., PHP, Python, Ruby) that can be uploaded to web servers to gain remote access and execute code on the server functions. They are also referred to as web shell scripts or simply web shells.
Section 1: Risks and Impact of Web Shell Backdoors
What risks do web shell backdoors pose?
Web shell backdoors pose severe risks to web servers and applications. Attackers can exploit vulnerabilities to gain unauthorized access, steal data, launch additional attacks, and persist within the network. They are difficult to detect and remove due to their ability to blend in with legitimate files and use encryption or obfuscation techniques.
Section 2: Prevention Measures for Web Shell Attacks
How can organizations prevent web shell attacks?
Organizations can take several prevention measures, including:
- Identifying and remediating vulnerabilities or misconfigurations in web applications and servers.
- Using web application firewalls (WAFs) to block known attack patterns and filter malicious requests.
- Leveraging SSL encryption to secure server communication.
- Employing endpoint detection and response (EDR) solutions for monitoring and analyzing server activity.
- Implementing zero-trust network principles to limit access and privileges of users and devices.
Exploring the Top 11 Jira Alternatives: Finding the Perfect Fit for Your Project Management Needs
Section 3: Detecting Web Shell Backdoors:
How can web shell backdoors be detected?
Several methods can aid in detecting web shell backdoors, including:
- Comparing files on the web server to known good files.
- Reviewing web traffic for unusual patterns.
- Matching time stamps of files on the web server to the time of upload.
- Reviewing web server folders and files for anomalies.
- Scanning for malicious code or signatures using antivirus or antimalware tools.
- Regularly patching web applications and servers to address vulnerabilities.
Section 4: Examples of Web Shell Backdoors
What are some examples of web shell backdoors?
Here are a few examples of web shell backdoors:
- Simple Shell: A minimalistic PHP web shell for executing commands and managing files and databases.
- B374K Shell: A PHP web shell with a user-friendly interface and features like file and database management.
- C99 Shell: A popular PHP web shell with various functionalities, including file management and system information viewing.
- R57 Shell: Similar to C99 Shell, it includes additional features such as self-deletion and shell binding to a TCP port.
- Wso Shell: A PHP web shell with features like file management, command execution, and server information retrieval.
What is the significance of understanding web shell backdoors?
Understanding web shell backdoors is crucial for individuals and organizations to protect their web servers and applications. By being aware of the risks involved, implementing preventive measures, and employing effective detection techniques, they can enhance their defense against web shell attacks and maintain a secure online environment.