Securing the IoT: Enhancing Device Protection with Firewalls
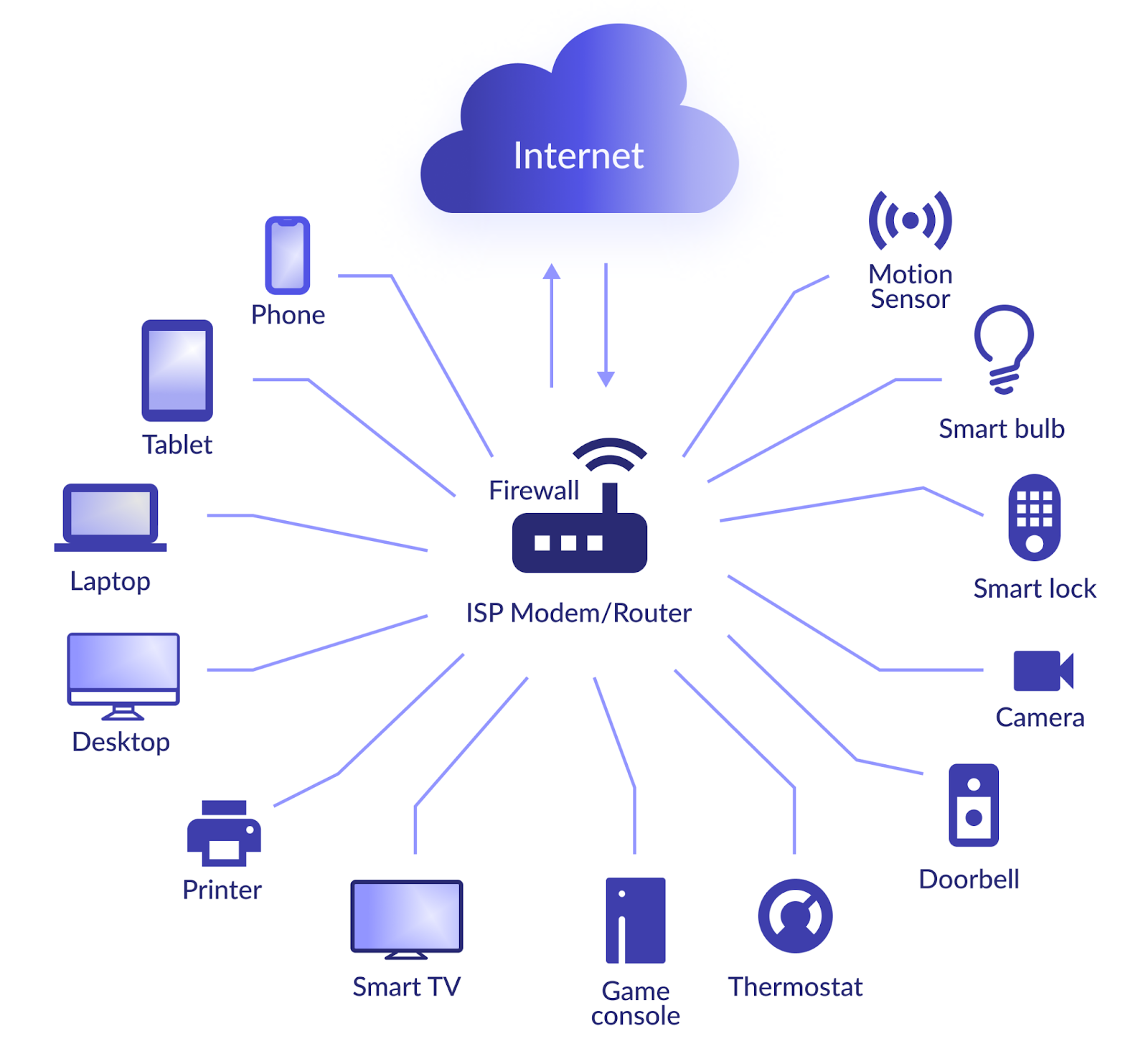
The rapid growth of the Internet of Things (IoT) has brought numerous benefits and convenience to our daily lives. From smart home devices to industrial sensors, IoT devices have become an integral part of modern society. However, with this interconnectedness comes an increased risk of cyber threats and vulnerabilities. In this blog post, we will explore the importance of securing IoT devices with firewalls and how they play a crucial role in protecting the connected world.
Understanding the IoT Security Challenge
The proliferation of IoT devices has created a vast attack surface for cybercriminals to exploit. These devices, often designed with limited processing power and security features, can become entry points for malicious activities if not adequately protected. Common vulnerabilities in IoT devices include weak default passwords, outdated firmware, and insufficient encryption protocols. Consequently, the need for robust security measures, such as firewalls, is essential to safeguard IoT ecosystems.
The Role of Firewalls in IoT Security
Firewalls have long been a cornerstone of network security, but their importance extends beyond traditional networks. When applied to IoT environments, firewalls act as a protective barrier between IoT devices and external networks. Here are several key ways in which firewalls contribute to securing IoT devices:
Network Segmentation
Firewalls enable the segregation of IoT devices into separate network segments, ensuring that compromised devices cannot directly access critical systems or sensitive data. By implementing access control rules, firewalls help prevent lateral movement within the network and limit the potential damage caused by an intrusion.
Traffic Filtering
Firewalls allow administrators to define and enforce strict rules for incoming and outgoing network traffic. By inspecting and filtering network packets, firewalls can identify and block suspicious activities, unauthorized access attempts, and potentially malicious communication from IoT devices.
Intrusion Detection and Prevention
Next-generation firewalls equipped with intrusion detection and prevention capabilities can actively monitor IoT device traffic for known attack patterns and anomalies. They can detect suspicious behaviors and take immediate action to prevent further compromise, such as blocking network connections or triggering alerts for investigation.
VPN and Secure Remote Access
For IoT devices deployed in remote locations or accessed by remote workers, firewalls can provide secure Virtual Private Network (VPN) connections. These encrypted tunnels ensure that communication between IoT devices and authorized users remains confidential and protected from eavesdropping or unauthorized access.
Threat Intelligence Integration
Advanced firewalls can leverage threat intelligence feeds to stay updated on the latest known threats and malware signatures. By incorporating real-time threat intelligence, firewalls can proactively identify and block connections to known malicious IP addresses or domains, adding an additional layer of protection to IoT devices.
Top 9 Free HTML Editors for Windows in 2023: Enhance Your Web Development Workflow
Threat Response and Incident Management
Firewalls can play a vital role in incident response and management for IoT devices. By logging and analyzing network traffic, firewalls provide valuable insights into potential security incidents or breaches involving IoT devices. This information can aid in identifying the source of an attack, understanding the extent of the compromise, and facilitating timely mitigation actions.
Behavioral Analysis and Anomaly Detection
Advanced firewalls equipped with behavioral analysis capabilities can establish baseline behavior patterns for IoT devices. By continuously monitoring and analyzing network traffic, firewalls can detect deviations from normal behavior, such as unusual data transfers or unauthorized device access. These anomalies can then trigger alerts or automated responses, enabling organizations to promptly investigate and respond to potential security incidents.
Secure Firmware and Patch Management
Firewalls can assist in enforcing secure firmware and patch management practices for IoT devices. By inspecting and controlling firmware updates and patches, firewalls ensure that only authorized and verified updates are applied to IoT devices. This helps prevent the installation of compromised or malicious firmware, reducing the risk of IoT device vulnerabilities being exploited.
Compliance and Regulatory Requirements
Many industries and sectors have specific compliance and regulatory requirements regarding the security of IoT devices. Firewalls can aid in meeting these requirements by providing necessary security controls, network visibility, and documentation for audits and assessments. By implementing firewalls as part of their IoT security strategy, organizations can demonstrate compliance and maintain a strong security posture.
Continuous Monitoring and Threat Intelligence Integration
Firewalls can be integrated into a comprehensive security monitoring and threat intelligence ecosystem for IoT devices. By collaborating with other security solutions such as Security Information and Event Management (SIEM) systems or threat intelligence platforms, firewalls can provide valuable data for threat detection, analysis, and incident response. This integration enhances the overall security posture of IoT environments and enables timely and informed decision-making in the face of emerging threats.
Securing IoT devices is crucial to protecting the connected world from cyber threats. Firewalls play a vital role in mitigating risks by implementing network segmentation, traffic filtering, intrusion detection, and secure remote access for IoT devices. By deploying firewalls specifically designed for IoT environments, organizations can strengthen their cybersecurity posture and ensure the integrity, confidentiality, and availability of their IoT deployments.
As the IoT landscape continues to expand, it is imperative for organizations and individuals to prioritize security measures and integrate firewalls into their IoT architectures. By doing so, we can confidently embrace the benefits of IoT technology while safeguarding ourselves against evolving cyber risks, ultimately building a more secure and connected world.